
学习写字楼新选择6000元主流配置,,这种配置需要考虑双核心的办公和娱乐平台,充分考虑办公室的办公需求和娱乐需求,以约6000元的预算和cost-e

酷睿I7 配置,配置,玩家国度啦华硕 Rampage II Extreme(3800元)如果米不够,也可以把Extreme改为Gene,不过是小板内存推荐金士顿6G DDR3 2000骇

固定路由器如何设置固定无线路由器设置教程,,如今我们的智能手机、平板电脑、笔记本、超级本等等都需要WiFi无线网络的支持,今天小编入手了
如何链接路由器设置TP链接无线路由器设置,,不管是什么品牌的无线路由器,首先第一步都是硬件安装,主要涉及的是将网线将电脑、(俗称猫)以及电脑

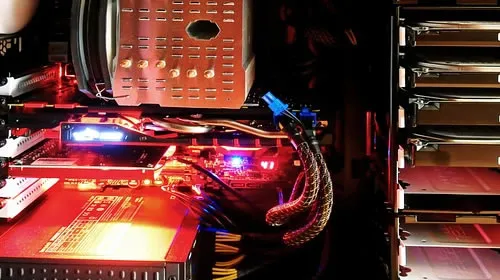
如何清除视频卡灰尘计算机图形卡的除尘过程,,冬天已经过去,温暖的春天和夏天的到来更近。电脑爱好者朋友,因为相对炎热的夏天,许多旧的电脑会

如何在安装过程中部署DevExpress控件,控件,文件,本文目录如何在安装过程中部署DevExpress控件请教devexpress的winform界面开发基本步骤de
提高3A四核羿龙II游戏配置的性能,,以节能环保为主题的IT产业,目前3A低端平台处理器、主板芯片组、独立开发卡性能突出,特别是在与AMD的处理

opporeno8参数配置及价格,面部,亿元,Oppo的荣誉2020年1月4日,接近屏幕关闭传感器是否支持双卡:支持oppor11splus什么时候上市的Oppo R11S P
查看配置:酷睿i3530集展示办公平台,,由于时间和精力的关系,我们不可能对所有的配置进行评论,希望我们能理解,我希望我们的评论能在那些需要帮

3500元超额值学生娱乐结构的优化配置,,作为一个DIY的主流用户领域的学生,每个用户51学生攒机的高峰。因为学生用户没有稳定的收入来源,攒机

高档万元i7//GTX460组装X58电脑配置推荐,,GTX460赢得了良好的声誉在开始上市,凭借其优异性能和适中的价格。许多消费者说,GTX460作为硬件核

路由器能加快速度吗教你如何加快速度限制,, 问答:我家和朋友用一个路由器上网,都是用一条线的,他看电影我就玩不成游戏,非常郁闷呀,我用的是电

电脑小白配置,求助各路装机大神指点?,小白,大神,各路,关于你这个问题我们需要从两个方面来回答你,我们先看看你的主要问题,第一个自选配置能不

2200元平台经济实用四核APU主机配置建议,,英特尔和平台间的较量已经DIY爱好者和鉴定人是无聊的,在这个问题上,虽然现在的AMD的市场份额和收

个人自配好的电脑|自己家用电脑配置,,1. 自己家用电脑配置CPU:Intel G系列奔腾双核主板:H81内存:4G显卡:集显机箱:100元以上电源:100元以


